Android app penetration testing – a detailed guide
Android's open system lacks stringent security barriers for apps on the Play Store. With 70,000 new monthly releases, counterfeit apps are proliferating easily.
These apps shared a common trait: they covertly collected user information such as locations, phone numbers, and email addresses. This data was then exploited for various nefarious purposes, from phishing attacks to selling it on the black market. While developing an Android app might seem straightforward, hackers can easily access your and your users' data without proper security measures. Conducting an Android app penetration testing is vital for safeguarding against potential cyber threats.
We can help you drive localization as a key initiative aligned to your business goals
What is Android app penetration testing?
Android penetration testing involves methodically identifying vulnerabilities within an Android application. Such testing aims to uncover security weaknesses before the application is released preemptively. If left unaddressed, these vulnerabilities can pose significant security risks.
Why is Android app penetration testing necessary?
Android apps are used today for various purposes, including mobile banking, shopping, messaging, social networking, and entertainment. From transferring money to ride-hailing, all these apps have a common ground – sharing personal information. For that reason, Android devices are vulnerable to various hacking techniques, including buffer overflow, code injection, reverse engineering, malware, and so on.
A valuable resource for developers is OWASP Mobile Top 10, a project built to identify the foremost vulnerabilities in mobile applications. These risks are determined by the project team through a comprehensive analysis of incident reports, vulnerability databases, and security assessments. The list of mobile controls is developed and upheld through collaboration between OWASP and the European Network and Information Security Agency (ENISA) to establish a unified set of controls.
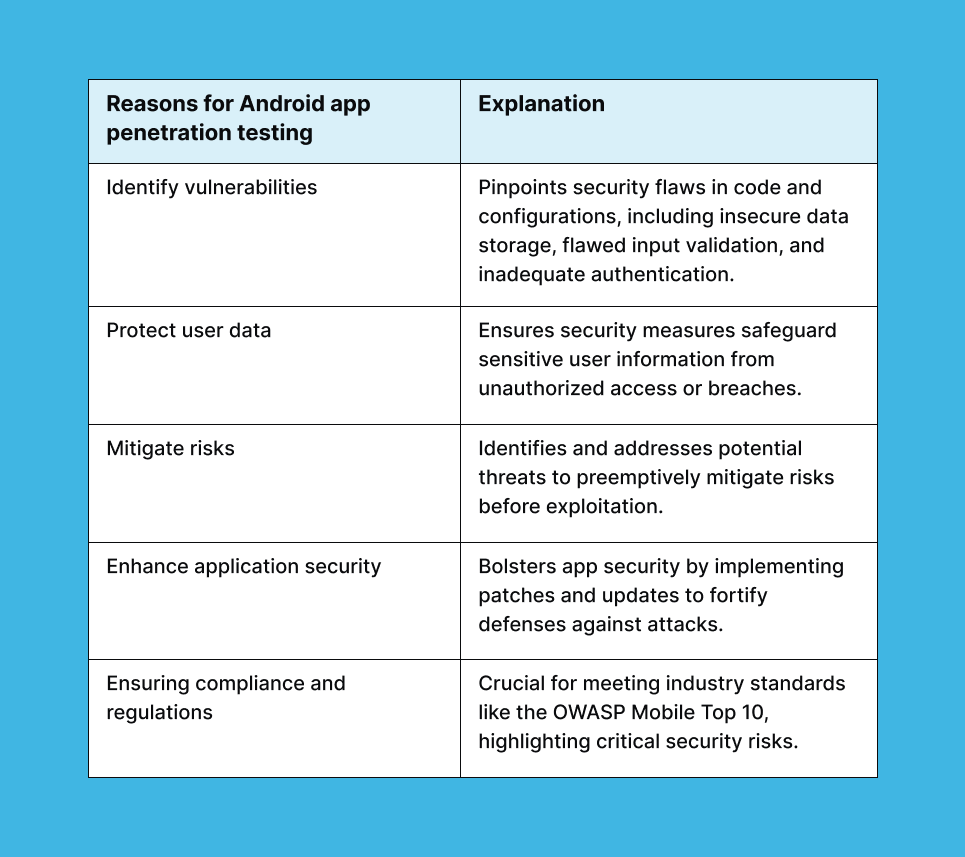
How to find vulnerabilities using OWASP Top 10 list
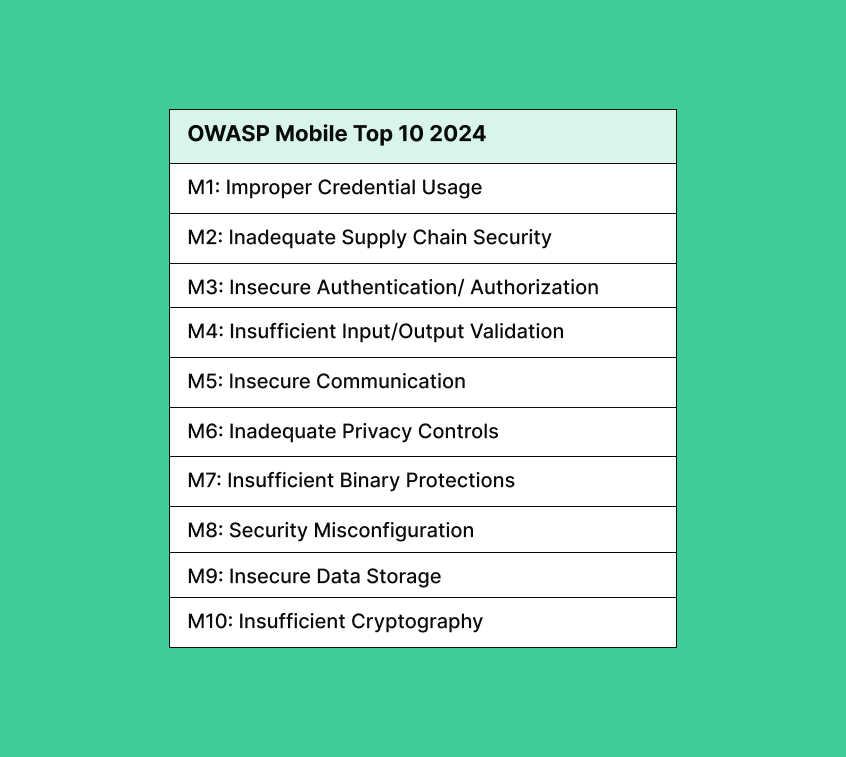
In 2016, OWASP released its list of Mobile Top 10 Vulnerabilities, but now we have a 2025 update. This list categorizes vulnerabilities based on their impact on individuals and businesses and provides suggestions for prevention.
If you're new to Android penetration testing, these vulnerabilities offer a solid starting point to identify flaws and enhance application security:
1. Improper credential usage
This category refers to security vulnerabilities in mobile applications where threat agents exploit hardcoded credentials or mishandle credentials.
Prevention:
- Avoid hardcoded credentials and use dynamic or encrypted credential storage methods instead.
- Utilize secure storage mechanisms and ensure proper validation of credentials.
- Conduct comprehensive security assessments to identify and rectify credential management weaknesses.
- Implement multi-factor authentication and robust authentication protocols to enhance security.
2. Inadequate supply chain security
Attackers may insert malicious code during development or exploit weaknesses in third-party software components, SDKs, vendors, or credentials to compromise the app or backend servers.
Prevention:
- Implement robust coding practices and conduct thorough code reviews to identify and rectify vulnerabilities.
- Ensure secure app signing processes and safeguard app signing keys and certificates.
- Assess the security of third-party software components and libraries used in the app.
- Implement encryption and robust security controls for data storage and transmission to prevent unauthorized access.
- Monitor the entire supply chain for vulnerabilities and implement security measures to detect and prevent malicious activities.
3. Insecure authentication/authorization
It refers to vulnerabilities within mobile applications exploited by threat agents through automated attacks.
Prevention:
- Utilize strong authentication protocols, multi-factor authentication, and secure session management.
- Enforce proper role-based access controls (RBAC) and privilege escalation prevention mechanisms.
- Employ security testing strategies to detect poor authentication and authorization schemes, such as binary attacks and execution of privileged functionality.
- Address the unique authentication requirements of mobile apps, considering offline usability while ensuring secure authentication processes.
- Encourage using strong passwords or passphrases instead of short passwords or 4-digit PINs.
4. Insufficient Input/Output validation
This refers to vulnerabilities arising from inadequate validation and sanitization of data from external sources, such as user inputs or network data.
Prevention:
- Thoroughly validate and sanitize user inputs to prevent manipulation by attackers.
- Validate and sanitize output data to prevent injection of malicious code and manipulation of displayed content.
- Consider specific contexts and expected data formats to prevent SQL injection or format string vulnerabilities.
- Validate data integrity to prevent data corruption or incorrect processing that could disrupt the application's functionality.
- Promote security awareness among developers, conduct comprehensive testing and code reviews, and ensure adherence to best practices in validation and sanitization techniques.
- Ensure compliance with data protection regulations and industry standards to mitigate legal and compliance issues.
5. Insecure communication
This category refers to vulnerabilities where data transmission occurs without adequate encryption or protection, allowing threat agents to intercept and modify the data exchanged between the mobile device and remote servers..
Prevention:
- Utilize modern cryptographic protocols such as SSL/TLS to encrypt data transmission and protect against interception.
- Securely configure encryption protocols, avoid using deprecated protocols or bad configuration settings, and enforce SSL certificate validation.
- Safeguard user data by minimizing data transmission over insecure channels and implementing additional security measures such as end-to-end encryption where applicable.
6. Inadequate privacy controls
Inadequate privacy controls involve flaws in protecting Personally Identifiable Information (PII) within mobile apps, making them susceptible to unauthorized access, manipulation, or deletion. PII encompasses sensitive data like names, addresses, credit card details, and personal beliefs.
Prevention:
- Implement robust encryption, access controls, and data protection protocols to safeguard PII.
- Adhere to data protection laws such as GDPR, CCPA, etc., to avoid legal penalties and ensure user privacy.
- Conduct thorough audits and tests to identify and address vulnerabilities in PII handling.
Only gather essential PII required for app functionality to reduce exposure risk.
7. Insufficient binary protections
Insufficient protection of app binaries refers to the vulnerability to unauthorized access, manipulation, or extraction of sensitive information.
Prevention:
- Implement obfuscation techniques to obscure sensitive code.
- Follow secure coding practices to minimize vulnerabilities.
- Encrypt sensitive data within binaries to prevent unauthorized access.
- Implement integrity checks to detect tampering.
- Use runtime protection mechanisms to prevent attacks.
- Digitally sign binaries and code to ensure authenticity.
- Continuously monitor for suspicious activities and apply timely security patches.
8. Security misconfiguration
Security misconfiguration in mobile apps is the improper setup of security settings, permissions, or controls, leaving vulnerabilities that unauthorized parties can exploit.
Prevention:
- Follow secure configuration guidelines.
- Conduct regular security audits.
- Ensure secure defaults and access controls.
- Use strong encryption and secure communication.
- Set appropriate file permissions and implement secure session management.
- Utilize automated tools for detection and remediation.
9. Insecure data storage
Threat agents, including cybercriminals, insiders, and state-sponsored actors, exploit vulnerabilities such as weak encryption and improper data handling to gain unauthorized access to valuable data.
Prevention:
- Adhere to established security standards for data storage and encryption.
- Conduct routine security audits to identify and rectify vulnerabilities.
- Implement robust encryption methods to protect sensitive data.
- Enforce strict access controls to limit unauthorized access to data.
- Employ secure data handling practices to prevent data tampering or leakage.
- Educate users about data security risks and best practices for protecting sensitive information.
- Conduct comprehensive testing to identify and address vulnerabilities in data storage mechanisms.
- Implement continuous monitoring to detect and respond to security incidents promptly.
10. Insufficient cryptography
Insufficient cryptography refers to inadequate or flawed cryptographic methods utilized to safeguard sensitive data, compromising its confidentiality, integrity, and authenticity.
Prevention:
- Utilize robust encryption algorithms and key management practices that adhere to industry best practices.
- Conduct routine security audits to identify and rectify vulnerabilities in cryptographic implementations.
- Implement secure key management practices to protect encryption keys from unauthorized access or misuse.
- Employ secure communication protocols, such as TLS/SSL, to encrypt data transmission between the mobile app and servers.
- Keep cryptographic libraries and protocols up-to-date with the latest security patches and updates to mitigate known vulnerabilities.
- Engage third-party security experts to conduct comprehensive assessments of cryptographic implementations to identify and address any weaknesses.
5 Steps for conducting Android app penetration testing
Performing penetration testing on an Android application is a systematic process to ensure its security against potential cyber threats. This comprehensive checklist delineates the essential stages to safeguard mobile apps effectively.
1. Surveillance and information gathering
Initiating the pen testing process involves gathering comprehensive information about the target application. This entails understanding its functionality, intended user base, underlying technologies, and potential external dependencies. Tools such as APK decompilers, network sniffers, and online research help gather valuable insights to establish a robust testing framework.
2. Threat modeling and risk assessment
After obtaining the necessary information, the tester proceeds to identify and prioritize potential threats and risks associated with the application. This phase involves assessing the application's attack surface, threat vectors, potential impact, and likelihood of exploitation. By understanding the critical assets and vulnerabilities, testers can formulate an effective testing strategy.
3. Analysis / Assessment
The analysis and assessment phase entails employing various techniques to evaluate the mobile application's security posture comprehensively:
- Static analysis: Scrutinizing the application's code and resources without execution to identify vulnerabilities such as insecure data storage or code injection.
- Dynamic analysis: Executing the application to observe runtime behavior and uncover vulnerabilities like insecure data transmission or flaws in authentication mechanisms.
- Architecture analysis: Evaluating the application's architecture to detect security vulnerabilities stemming from architectural flaws.
- Reverse engineering: Dissecting the application to understand its inner workings, even without access to the source code.
- Analysis of file system: Examining the application's file system to identify insecurely stored sensitive data.
- Inter-application communication: Analyzing communication mechanisms between different applications within the system for potential vulnerabilities.
4. Exploitation
The exploitation phase involves exploiting identified vulnerabilities to assess their impact and potential for unauthorized access or data compromise. Pen testers conduct targeted attacks to gain unauthorized access, escalate privileges, or manipulate the application's behavior. Typical attack vectors such as SQL injection and cross-site scripting are also tested.
5. Reporting
Upon completing the testing process, testers compile a detailed report outlining identified vulnerabilities, their severity, and recommended remediation steps. This report serves as a roadmap for developers and stakeholders to prioritize fixes and effectively enhance the application's security posture.
What are the benefits of Android app penetration testing?
Android application testing offers the advantage of identifying and addressing potential vulnerabilities within your application before its release. Additionally, it provides the following benefits:
- Safeguarding your company's reputation for security.
- Mitigating the risk of legal issues arising from data leaks.
- Ensuring the safety and security of your company's customers' data.
- Protecting your company's confidential data.
- Ensuring compliance with local security assessment requirements.
Best practices for Android penetration testing
To ensure a high-quality experience for app users, follow mobile app testing best practices:
1. Understand the security framework
Gain a comprehensive understanding of the security framework employed by the Android application. This knowledge allows for creating a robust penetration testing plan that assesses all necessary aspects of the application's security.
2. Familiarize yourself with the application structure
Acquire an in-depth understanding of the application's structure, including how it operates, manages data in the backend, interacts with other services, and handles user requests.
3. Select appropriate penetration testing tools
Choose penetration testing tools that can conduct thorough tests to detect vulnerabilities within the Android application. The preferred methodology for Android application penetration testing is often black-box testing, where the tester has limited prior knowledge about the application.
Android penetration testing utilizes various tools, including open-source:
- MobSF: An all-in-one framework for mobile app pen-testing, malware analysis, and security assessment, supporting static and dynamic analysis.
- Frida: A dynamic instrumentation toolkit favored by developers, reverse engineers, and security researchers.
- Apktool: Used for reverse engineering/decompiling apk files, aiding in discovering sensitive data.
Other tools worth mentioning are Cobalt, Astra Pentest, Intigriti, and others.
How Global App Testing enhances your app security
Global App Testing (GAT) specializes in functional bug identification, payment testing, and UX issue resolution. Although we are not a pen testing service per se, here's how GAT can enhance your app security:- Scalable crowdsourced testing: Combines scalability with detailed analytics and a comprehensive testing suite to efficiently test across various devices, OSs, and markets.
- Global network of testers: Utilizes over 90,000 professional testers worldwide to ensure thorough testing under real-world conditions.
- Streamlined testing process: Clients define testing tasks, distributed to matching testers, with real-time feedback and reports for quick issue resolution.
- Quality Assurance: Validates each bug report and feedback item for accuracy and relevance, providing actionable data for clients.
Additionally, Global App Testing prioritizes data integrity, availability, and confidentiality, achieving ISO 27001 Certification in 2023. Operating on AWS ensures advanced security architecture, with robust encryption protocols and authentication mechanisms safeguarding data.
Integrated disaster recovery and business continuity plans maintain high availability infrastructure, complemented by firewall protection and secure build distribution protocols. Employee security is prioritized through mandatory training and referral checks, ensuring GDPR compliance and adherence to ISO 27001-aligned policies and procedures. If you want to learn more about our services, let's schedule a call today!
We can help you drive global growth, better accessibility and better product quality at every level.
Keep learning
11 Mobile testing trends you need to know about
The 8 best web app development software products, according to our editors
AI testing - everything you need to know
